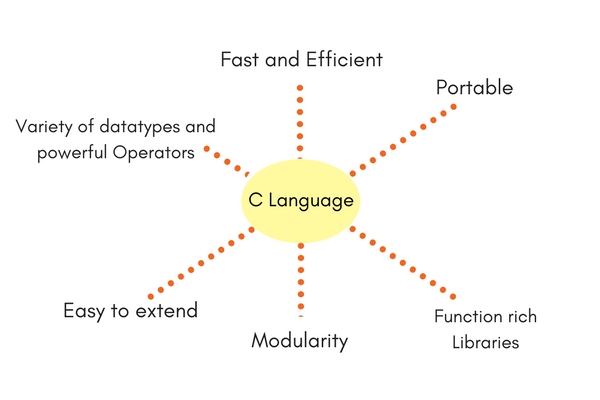
In the C programming, data types specify an extensive system used for declaring variables or functions of different types. The C data type of a variables determines how much space it occupies in memory and how the bit pattern stored in memory will be understand by processor.
Various arithmetic datatypes and functional datatypes available in C programming language are enlist below
Various arithmetic datatypes and functional datatypes available in C programming language are enlist below
Basic data types Of C language:
integer type
This type is used to define integer numbers. It is denoted as "int" in the C programs in this c programming tutorial
{
int number;
number = 5;
}
{
int number;
number = 5;
}
Floating-point types.
This type is used to define decimal numbers. It will be denoted as "float" in the c language
{
float Miles;
Miles = 5.6;
}
float Miles;
Miles = 5.6;
}
Boolean type
The Boolean type is used to define a variable that consists of only two values true or false
{
{
bool b = getc(stdin) == 't' ? true : false;
}
double - data type
Double in c language is used to define BIG decimal point numbers. The memory reserved for this datatype is twice as compared to int datatype. Likely to be 8 bytes.
Double in c language is used to define BIG decimal point numbers. The memory reserved for this datatype is twice as compared to int datatype. Likely to be 8 bytes.
{
double Atoms;
Atoms = 2500000;
}
char - data type
char data type defines characters in a c program.
{
char alphabet;
alphabet = 'x';
}
double Atoms;
Atoms = 2500000;
}
char - data type
char data type defines characters in a c program.
{
char alphabet;
alphabet = 'x';
}
Enumerated types in C language:
They are also arithmetic types and they are used to define variables that can only be assigned certain discrete integer values throughout the c program.
They are also arithmetic types and they are used to define variables that can only be assigned certain discrete integer values throughout the c program.
The type void:
The type specified void returns no value, meaning no value is available. It is used mainly in functions which returning null or no value.
The type specified void returns no value, meaning no value is available. It is used mainly in functions which returning null or no value.
Derived types in C programming:
They include (a) Pointer types, (b) Array types, (c) Structure types, (d) Union types and (e) Function types. Which will be detailed in the next chapters
They include (a) Pointer types, (b) Array types, (c) Structure types, (d) Union types and (e) Function types. Which will be detailed in the next chapters